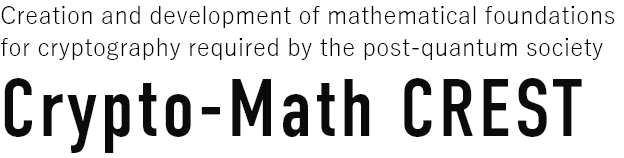About Crypto-Math CREST
This research project is supported by CREST – a funding program, which is run by the Japan Science and Technology Agency (JST). The aims of JST are to promote and encourage the development of breakthrough technologies that contribute to attainment of the country’s strategic objectives, and to return the results of such research to the society through innovations.
CREST supports team-oriented research with the aim of achieving the strategic goals set forth by the government. The objective is to create revolutionary technological seeds for science and technology innovation. Detailed information can be found on the JST CREST websites.
- Research area
- [Mathematical Information Platform] Creating information utilization platform by integrating mathematical and information sciences, and development to society
https://www.jst.go.jp/kisoken/crest/en/research_area/ongoing/area2019-4.html - Project Title
- Creation and development of mathematical foundations for cryptography required by the post-quantum society
- Project leader
- Tsuyoshi Takagi,
Professor, Graduate School of Information Science and Technology, The University of Tokyo - Co-Investigators
- Masato Wakayama,
Fundamental Mathematics Research Principal, NTT Communication Science Laboratories
Noboru Kunihiro,
Professor, Faculty of Engineering, Information and Systems, University of Tsukuba
Keisuke Tanaka,
Professor, Graduate School of Information Science and Engineering, Tokyo Institute of Technology
Evolution of cryptography
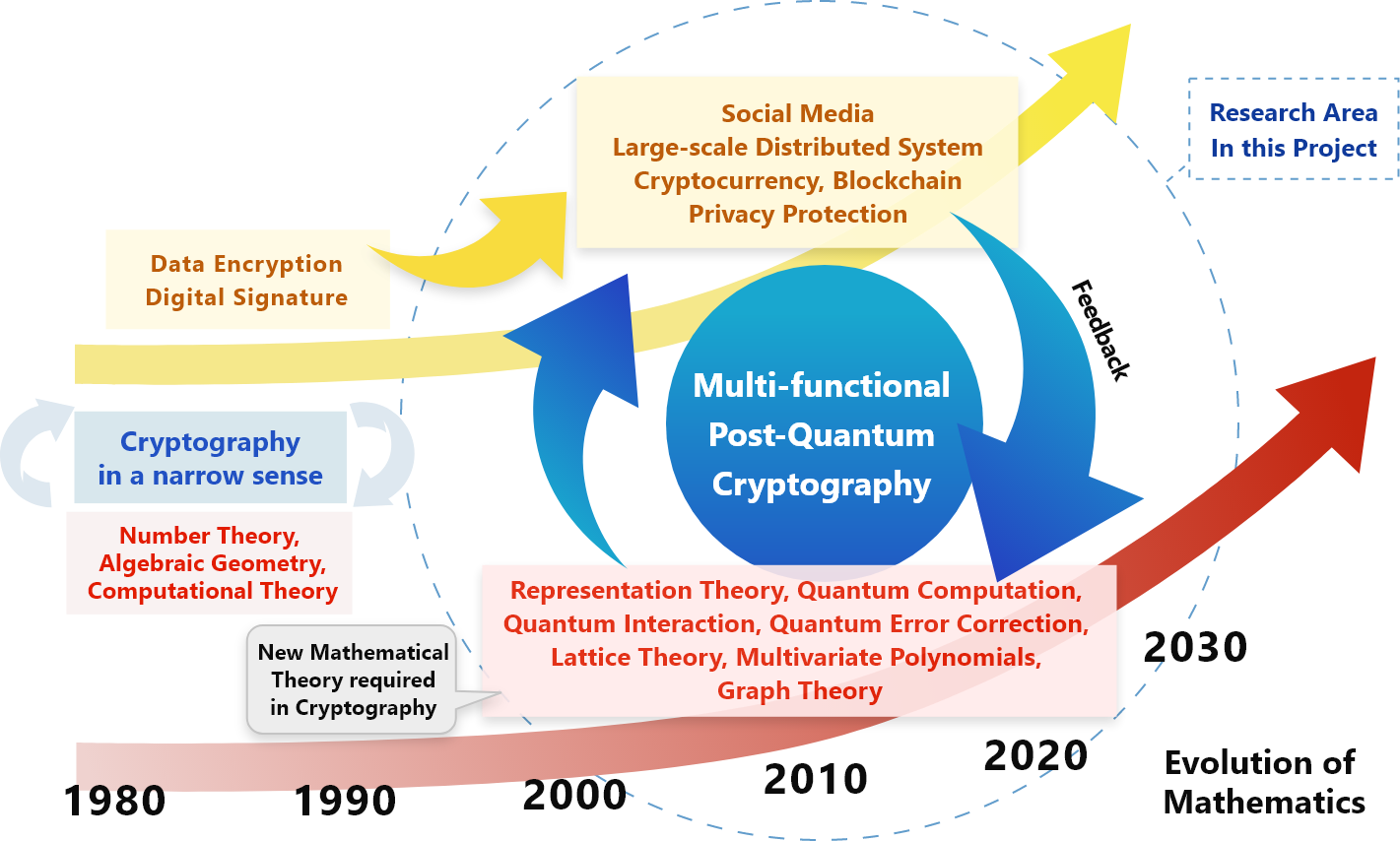
In this research project, to avoid the compromising cryptographic systems, we consider various possible attackers including those using quantum computers and side-channel attacks conducted through a power analysis. We plan to research on mathematical foundations aimed at the realization of cryptographic technology resistant to such attacks.
Furthermore, we will build a cryptographic system with a decentralized security function.
Research Objectives
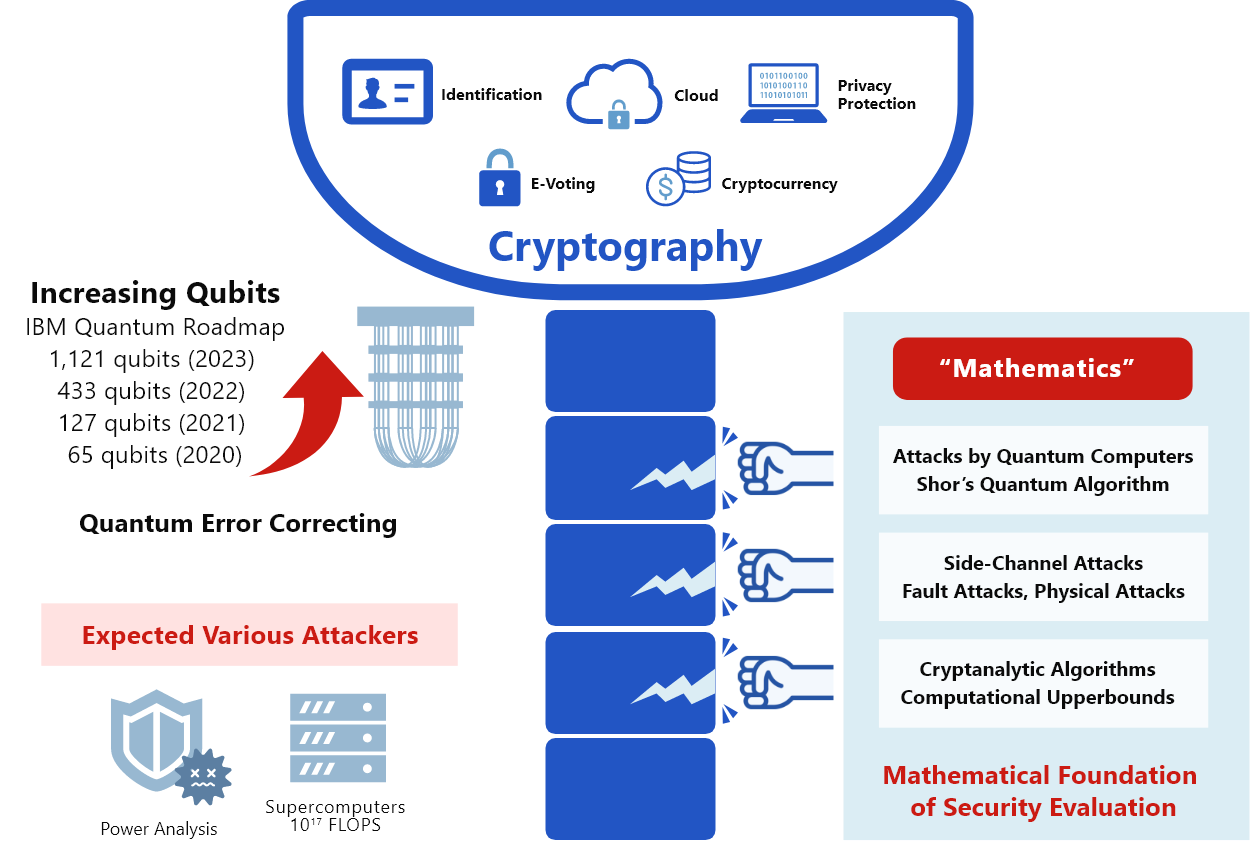
RSA cryptography and elliptic curve cryptography, which are widely used for data encryption and digital signatures, are constructed using pure mathematics including number theory and algebraic geometry. Furthermore, as cryptography continues to evolve, we recently started using cryptographic protocols of large-scale distributed systems such as cryptocurrencies and blockchains as well as personal authentication for privacy protection. However, these cryptographic technologies can be compromised using quantum computers, and research and development of post-quantum cryptography based on mathematical theories such as representation theory, lattice theory, and multivariate polynomials, involving industry, government, has been accelerating.
We plan to develop a cryptographic technology that can be securely used even in a post-quantum society, in which the performance of quantum computers will improve and become widespread through the efforts of mathematicians who are strongly interested in the field of mathematics t pioneered by cryptography. We aim to deepen the basic mathematics of post-quantum cryptography, model the strongest possible attacks such as side-channel attacks, and constructing cryptographic protocols that guarantee security against such attacks.
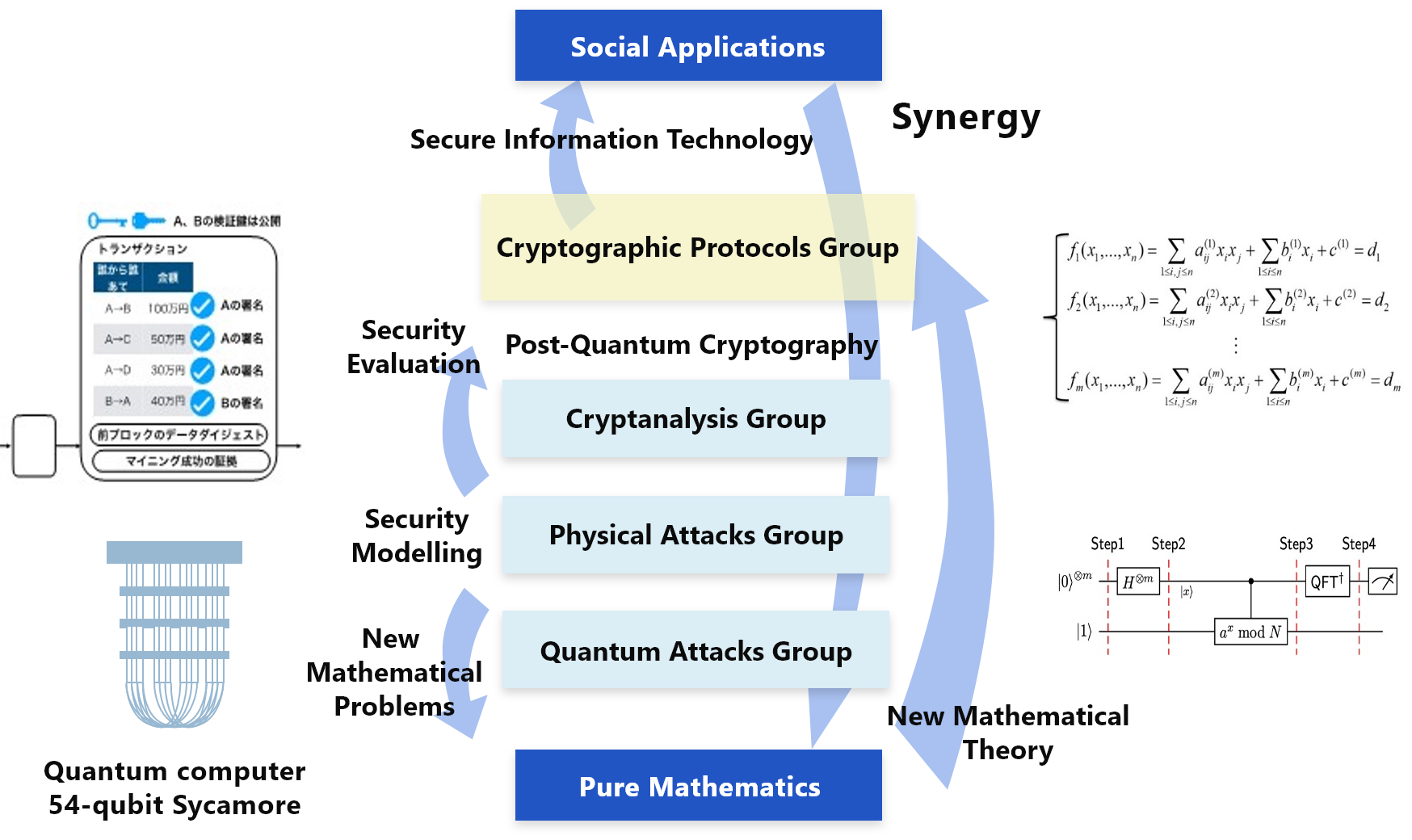
Our Groups
In the construction of cryptographic systems that can be securely applied even in the era of quantum computing, we will not only evaluate the difficulty of computational problems that are the basis of security, but also consider the knowledge of quantum computers and quantum algorithms and their use in an actual environment. It will also be necessary to consider the resistance to side-channel attacks, and the design of cryptographic protocols with quantum resistance based on these attack models is an academically challenging research theme. In this research project, in addition to the “Cryptanalysis group,” “Quantum attacks group,” and “Physical attacks group,” our research project has a fourth group called the “Cryptographic protocols group” for development of multifunctional cryptosystems that are resistant to such attacks.
Future Research Perspectives
The cryptographic security evaluation model obtained in this research project will enable an accurate evaluation of various attacks by quantum computers and physical observations, and eventually a robust cryptographic method can be realized. Furthermore, a method for achieving a security evaluation of post-quantum cryptography through this study constructed here will be the basis for a further evolution and will bring about a great spillover effect both academically and practically. In addition, cryptographic protocols based on post-quantum cryptography as a primitive can be used as a security base for the personal authentication of social media and blockchain used in cryptocurrencies.
By promoting this research project, an environment will be constructed in which mathematicians with various specialties, and researchers in the fields of cryptography and quantum information, can collaborate. Because this collaborative field will function as a research base for post-quantum cryptography, it is expected that our presence in this field will increase internationally.